CertiK exec explains how to keep crypto safe after $1.4B Bybit hack
19 Marzo 2025 - 3:30PM
Cointelegraph

The February hack against Bybit sent ripples through the
industry after $1.4 billion in Ether-related tokens was stolen from
the centralized exchange, reportedly by the North Korean hacking
collective Lazarus Group, in what was the most costly crypto theft
ever.
The fallout from the hack has left many people wondering what
went wrong, whether their own funds are safe, and what should be
done to prevent such an event from happening again.
According to blockchain security company CertiK, the massive
heist represented
roughly 92% of all losses for February, which saw a nearly
1,500% increase in total lost crypto from January as a result of
the incident.
On Episode 57 of Contelegraph’s The Agenda podcast,
hosts Jonathan DeYoung and Ray Salmond speak with CertiK’s chief
business officer, Jason Jiang, to break down how the Bybit hack
happened, the fallout from the exploit, what users and exchanges
can do to keep their crypto secure, and more.
Are crypto wallets still safe after Bybit hack?
Put simply, Lazarus Group was able to pull off the massive hack
against Bybit because it managed to compromise the devices of all
three signers who controlled the multisignature SafeWallet Bybit
was using, according to Jiang. The group then tricked them into
signing a malicious transaction that they believed was legit.
Does this mean that SafeWallet can no longer be trusted? Well,
it’s not so simple, said Jiang. “It is possible that when the Safe
developer’s computer got hacked, more information was leaked from
that computer. But I think for the individuals, the likelihood of
this happening is rather low.”
He said there are several things the average user can do to
drastically increase their crypto security, including storing
assets on cold wallets and being aware of potential phishing
attacks on social media.

Source: CertiK
When asked whether hodlers could see their Ledger or Trezor
hardware wallets exploited in a similar manner, Jiang again said
that it’s not a big risk for the average user — as long as they do
their due diligence and transact carefully.
“One of the reasons that this happened was that the signers were
like a blind-send-signing the order, just simply because their
device did not show the full address,” he said, adding, “Make sure
that the address you are sending to is what you’re intending to,
and you want to double check and triple check, especially for
larger transactions.”
“I think after this incident, this is probably going to
be one of the things the industry will try to correct itself, to
make the signing more transparent and easier to recognize. There
are so many other lessons being learned, but this is certainly one
of them.”

How to prevent the next multibillion-dollar exchange hack
Jiang pointed to a lack of comprehensive regulations and
safeguards as a potential element contributing to the ongoing
fallout from the hack, which fueled debates over the limits of
decentralization after
several validators from crosschain bridge THORChain refused to
roll back or block any of Lazarus Group’s efforts to use the
protocol to convert its funds into Bitcoin
(BTC).
“Welcome to the Wild West,” said Jiang. “This is where we are
right now.”
“From our view, we think crypto, if it is to be flourishing, it
needs to hug the regulation,” he argued. “To make it easy to be
adopted by the mass general here, we need to hug the regulation,
and we need to figure out ways to make this space safer.”
Related:
Financial freedom means stopping crypto MEV attacks —
Shutter Network contributor
Jiang commended Bybit CEO Ben
Zhou on his response to the incident, but he also pointed out
that the exchange’s bug bounty program prior to the hack had a
reward of just $4,000. He said that while most people in
cybersecurity are not motivated by money alone, having larger bug
bounties can potentially help exchanges stay more secure.
When asked about the ways exchanges and protocols can motivate
and retain top-tier talent to help protect their systems, Jiang
suggested that security engineers don’t always get the credit they
deserve.
“A lot of people say that the first-degree talent goes to the
developers because that’s where they will get most rewarding,” he
said. “But it’s also about us giving enough attention to the
security engineers. They carry a huge responsibility.”
“Cut them some slack and try to give them more credit.
Whether it’s monetary or whether it’s recognition, give them what
we can afford, and make it reasonable.”
To hear more from Jiang’s conversation with The Agenda
— including how CertiK carries out audits, how quantum computing
and AI will impact cybersecurity, and more — listen to the full
episode on Cointelegraph’s Podcasts page,
Apple
Podcasts or Spotify. And don’t
forget to check out Cointelegraph’s full lineup of other shows!
Magazine:
Bitcoin vs. the quantum computer threat — Timeline and
solutions (2025–2035)
This article is for
general information purposes and is not intended to be and should
not be taken as legal or investment advice. The views, thoughts,
and opinions expressed here are the author’s alone and do not
necessarily reflect or represent the views and opinions of
Cointelegraph.
...
Continue reading CertiK exec explains how to keep
crypto safe after $1.4B Bybit hack
The post
CertiK exec explains how to keep crypto safe after
$1.4B Bybit hack appeared first on
CoinTelegraph.
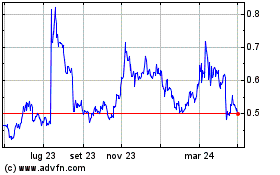
Grafico Azioni Ripple (COIN:XRPUSD)
Storico
Da Mar 2025 a Mar 2025
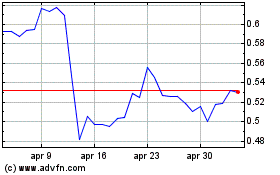
Grafico Azioni Ripple (COIN:XRPUSD)
Storico
Da Mar 2024 a Mar 2025