New MassJacker malware targets piracy users, steals crypto
14 Marzo 2025 - 10:20PM
Cointelegraph


A previously unknown type of cryptojacking malware called
MassJacker is targeting piracy users and hijacking crypto
transactions by replacing stored addresses,
according to a March 10 report from CyberArk.
The cryptojacking malware originates from the website
pesktop[dot]com, where users seeking to download pirated software
may unknowingly infect their devices with the MassJacker malware.
After the malware is installed, the infection swaps out crypto
addresses stored on the clipboard application for addresses
controlled by the attacker.
According to CyberArk, there are 778,531 unique wallets linked
to the theft. However, only 423 wallets held crypto assets at any
point. The total amount of crypto that had either been stored or
transferred out of the wallets amounted to $336,700 as of August.
However, the company noted that the true extent of the theft could
be higher or lower.
One wallet, in particular, seemed active. This wallet contained
just over 600 Solana (SOL) at the time of analysis, worth approximately
$87,000, and had a history of holding non-fungible tokens. These
NFTs included Gorilla Reborn and Susanoo.
Related: Hackers have started using AI to churn out
malware
A look into the wallet on Solana’s blockchain explorer Solscan
shows 1,184
transactions dating back to March 11, 2022. In addition to
transfers, the wallet’s owner dabbled in decentralized finance in
November 2024, swapping various tokens like Jupiter
(JUP), Uniswap
(UNI), USDC
(USDC), and
Raydium (RAY).
Crypto malware targets array of devices
Crypto malware is not new. The first publicly available
cryptojacking script was released by
Coinhive in 2017, and since then, attackers have targeted an
array of devices using different operating systems.
In February 2025, Kaspersky Labs said that it
had found crypto
malware in app-making kits for Android and iOS. The malware had
the ability to scan images for crypto seed phrases. In October
2024, cybersecurity firm Checkmarx revealed it
had discovered
crypto-stealing malware in a Python Package Index, which is a
platform for developers to download and share code. Other crypto
malware have targeted
macOS devices.
Related: Mac
users warned over malware ‘Cthulhu’ that steals crypto
wallets
Rather than having victims open a suspicious PDF file or
download a contaminated attachment, attackers are getting sneakier.
One new “injection method” involves the fake job scam, where an
attacker will recruit
their victim with the promise of a job. During the virtual
interview, the attacker will ask the victim to “fix” microphone or
camera access issues. That “fix” is what installs the malware,
which can then drain the victim’s crypto wallet.
The “clipper” attack, in which malware alters cryptocurrency
addresses copied to a clipboard, is less well-known than ransomware
or information-stealing malware. However, it offers advantages for
attackers, as it operates discreetly and often goes undetected in
sandbox environments, according to CyberArk.
Magazine: Real
AI use cases in crypto, No. 3: Smart contract audits &
cybersecurity
...
Continue reading New MassJacker malware targets
piracy users, steals crypto
The post
New MassJacker malware targets piracy users, steals
crypto appeared first on
CoinTelegraph.
Grafico Azioni Sandbox (COIN:SANDUSD)
Storico
Da Mar 2025 a Apr 2025
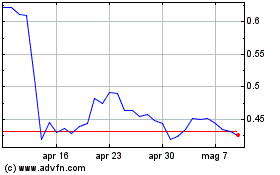
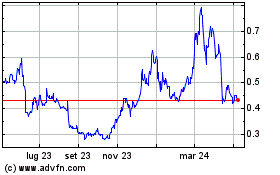
Grafico Azioni Sandbox (COIN:SANDUSD)
Storico
Da Apr 2024 a Apr 2025